Email spam filters keep your inbox free from scams, malware, and other nasties—but scammers always adapt. A new email scam technique known as email salting is helping attackers bypass your email protection, but there are a few ways to keep your inbox safe.
How Email Salting Works
Email salting is a nasty tactic in which scammers manipulate the content of an email (most commonly by distorting the underlying HTML code) to fool spam filters. Your browser translates the HTML code into what you see on screen, and by using different tricks, a scammer can add junk to the code, bypassing the filter while ensuring that regular text is displayed on screen.
For instance, it’s possible to add zero-width space and zero-width non-joiner characters into the HTML code. In layman’s terms, an email will display a word that often triggers spam filters while the underlying code is filled with filler characters.
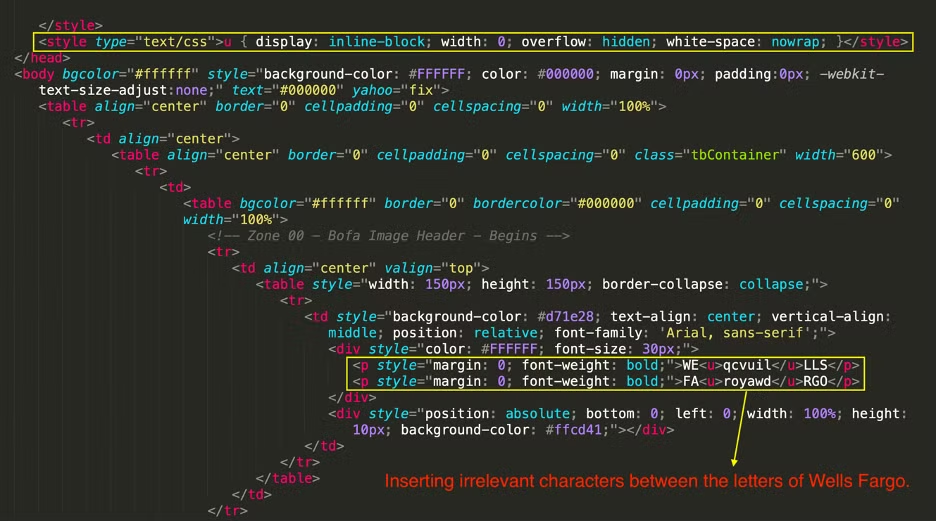
A good example is the word WELLS FARGO. With email salting, the right phrase will be displayed, but on closer inspection of the HTML, the actual string of characters will be WEqcvuilLLS FAroyawdRGO.
Related
Scammers Have Found a Way to Sneak Emails Into Your Inbox
A sneaky trick allows malicious emails to dodge your spam filter.
This isn’t the only way to pull this off. A much simpler technique, such as homoglyph attacks, can be equally damaging. It involves replacing some of the characters with those that are similar but are encoded differently. A good example is replacing the regular ‘o’ with one from the Cyrillic alphabet since they appear almost identical but have a different Unicode (a text encoding standard).
Not only may this fool some spam filters, but it is also enough to trick you into thinking that the sender is legitimate.
A picture is worth a thousand words, which is why I had to break my oath and make a few homoglyphs. I’ll go easy on you:
- Bank of America
- Bank of America
I simply replaced an “o” with a similar-looking character, and while it may look obvious, I did say I’ll go easy on you. Let’s try a trickier one:
- Bank of America
- Bank оf America
Impossible to tell apart and super easy to pull off with the Cyrillic alphabet switcheroo (the second example is the “salted” one).
Another way scammers can bypass your filters is to use images instead of text. That one is easy to recognize for most people because no legitimate services will ever replace text with an image, especially if they’re warning you of a data breach or whatever phishing scammers are up to these days.
How to Spot an Email Salting Attack
Short answer: no.
Although shady individuals now use AI to craft more effective phishing emails, this scam is still easy to spot if you’re familiar with the major tells. Consider your spam filter as just the first line of defense against phishing, so if a scammy email somehow manages to get through, it’s not the end of the world.

Related
AI Phishing Attacks Are Everywhere, and This Is How I Spot Them
Scammers use AI to make attacks more convincing than ever, but there are still some tell-tale signs.
To easily determine the sketchy status of the email, take a close look at the overall message.
Most phishing scams fall apart as soon as you ask yourself why a legitimate business is trying to get you to act so quickly by redirecting you to a whole new site or urging you to download an attachment ASAP. Scammers use social engineering tricks to manipulate you into acting quickly, but if you take a breather, you’ll probably see right through the charade.
Even if the email looks genuine, it’ll lack the personal details the company should have on hand. For example, they may refer to you as a “Dear Customer” or something along those lines.
Although homoglyphs can make things a bit trickier to catch on to, the email address the scammers use may be off. You’ll see that the domain name is a variation of the official one, or if the scammers are lazy, a regular Gmail account that no self-respecting business would use.
But say you don’t detect any of these signs in the email you received—should you still follow its instructions?
Source View is Your Best Friend
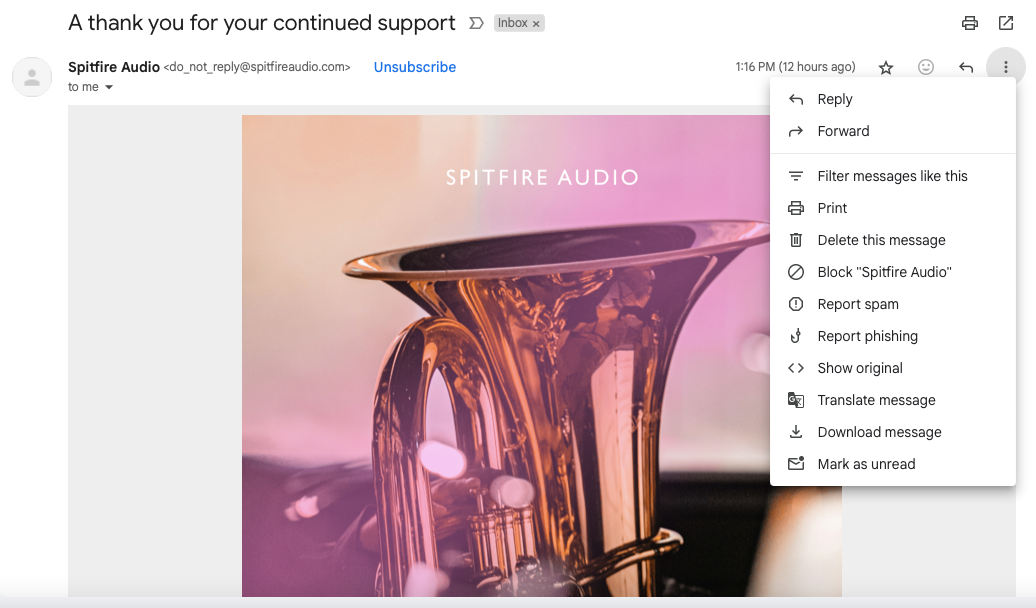
To check if an email is salted, you should sneak a glance at the HTML code through Source View. Most email clients have this option, but I’m using Gmail as an example.
Click the three dots on the top right corner of the email and choose “Source View” in the dropdown list. You’ll be able to see the inner workings of the email.
It’s apparent that the body of the message is completely intact and identical to what is shown on the front end of the email: no random characters breaking up select words, no hidden code.
Remember our Wells Fargo example from earlier? The HTML code paints a clear picture. There is a bunch of irrelevant characters inserted between the words Wells and Fargo.
Unfortunately, it was nearly impossible to find a salted email, but this example approximates what you’ll see in the source view if the email code has been tampered with.
What About Homoglyph Attacks?
Email salting attacks are similar to homoglyph attacks. If the email seems legitimate but you still have a weird feeling about it, it’s smart to put on your investigative glasses and start looking for some shady characters.
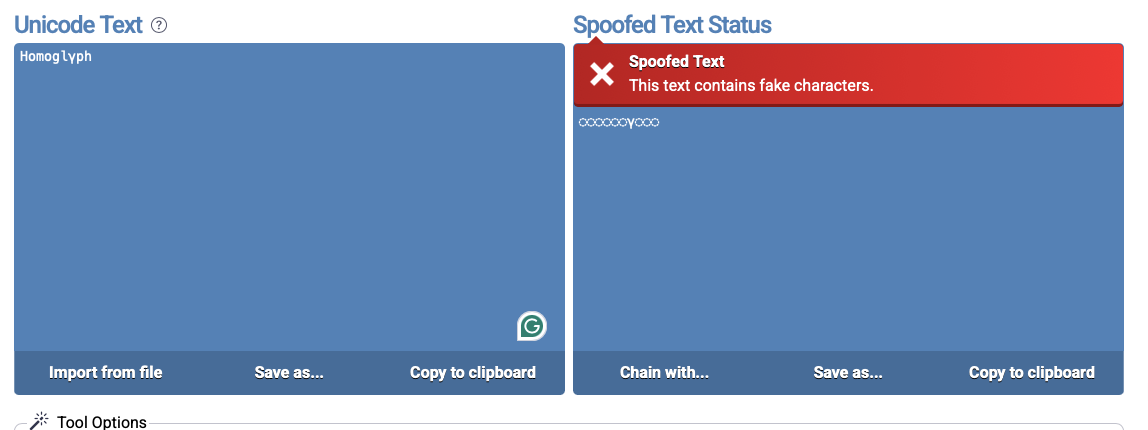
Pay close attention, and you’ll quickly be able to tell which character is wrong:
If you guessed ‘’y”, you’re correct. It stands out as a sore thumb if you know what you’re looking for.
However, while I believe we should all develop a keen eye for detail to avoid falling for scams, there are also plenty of tools online for spotting homoglyphs you can use. Spoofed Unicode Checker is my favorite: simply copy the text in the left window, and the tool will show you which characters are spoofed.
With this knowledge and a new set of tools in your arsenal, you’ll be able to effectively protect yourself against phishing if one email makes it past your spam filter. Though scams are more sophisticated with the infusion of AI, practicing common sense and being aware of the main signs of phishing will go a long way in helping you avoid falling prey to such tactics.