Virtual private networks (VPNs) have become a go-to solution for online privacy and accessing geo-restricted content. However, they’re not always the best fit for everyone. Whether you’re looking for a budget-friendly option, faster speeds, or simply an alternative, several VPN alternatives exist.
1 Try Smart DNS
Smart DNS is a popular alternative for those wanting to access geo-restricted content without encryption. This service works by rerouting your Domain Name Server (DNS) queries through its own servers. While it doesn’t provide the same level of security as a VPN, smart DNS allows you to access sites that might otherwise be blocked in your location.
One of the key advantages of smart DNS is its speed. Since it doesn’t encrypt your internet traffic, it can often provide a faster connection than VPNs. This makes it particularly appealing for streaming videos or gaming, where buffering can be a significant annoyance.
To use smart DNS, you typically sign up with a service provider like Unlocator or Smart DNS Proxy, then configure your device’s DNS settings to the smart DNS servers provided. Most services offer straightforward setup guides for various devices and platforms.
However, it’s essential to remember that smart DNS does not hide your IP address. This means it’s not suitable for those prioritizing security and privacy. If your primary goal is to access restricted content, smart DNS could be an excellent option without the extra cost of a VPN.
2 Route Your Traffic Through a Proxy Server
Proxy servers are another option for those looking to hide their IP addresses and access restricted websites. They act as intermediaries between your device and the internet, routing your internet traffic through their IP addresses and making it harder for others to trace your online activities back to you.
There are several benefits to using a proxy server. For one, many are often free, making them an attractive choice for budget-conscious users. HideMyAss and KProxy are popular free options that can help bypass geographic restrictions effectively.
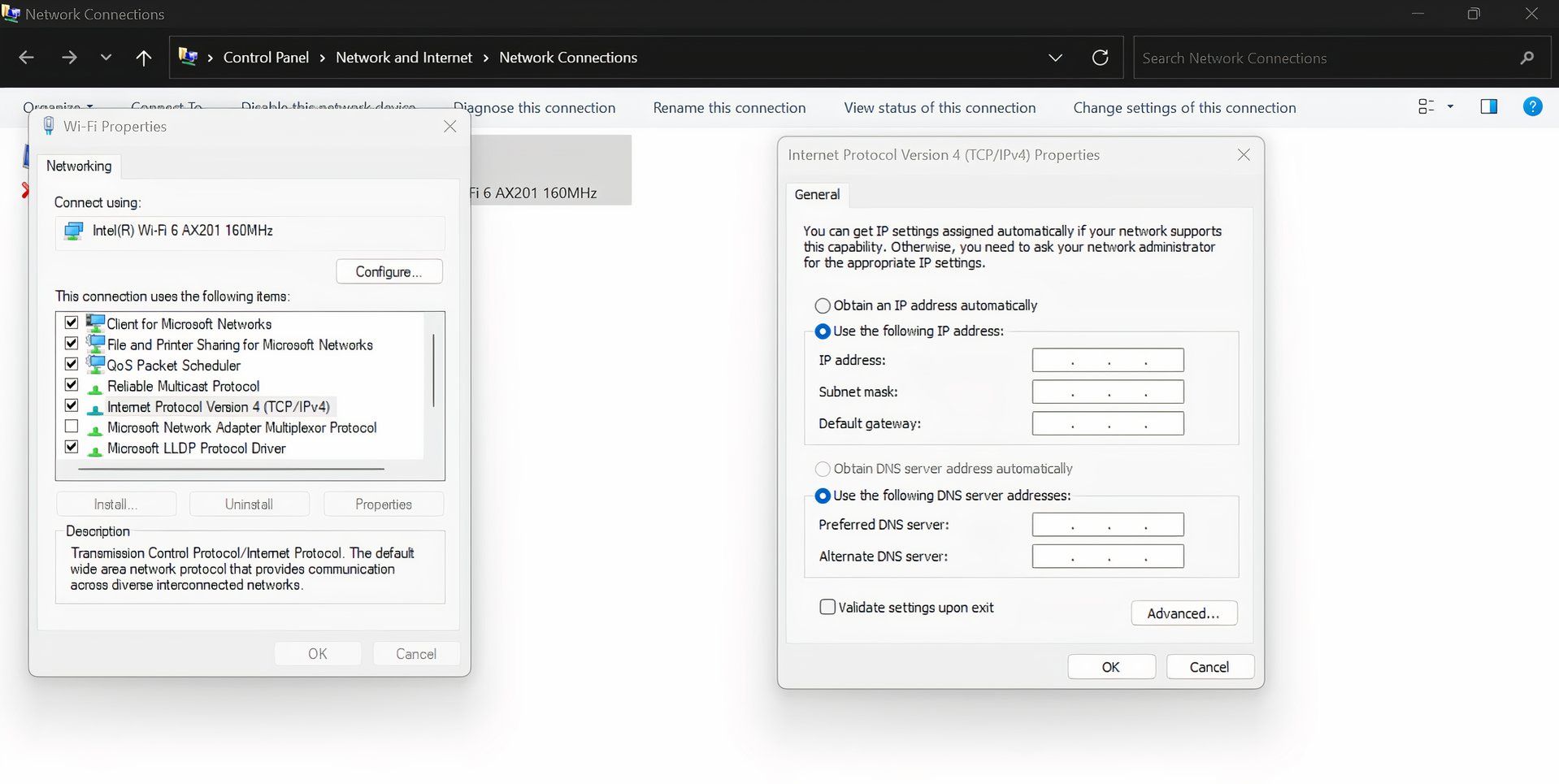
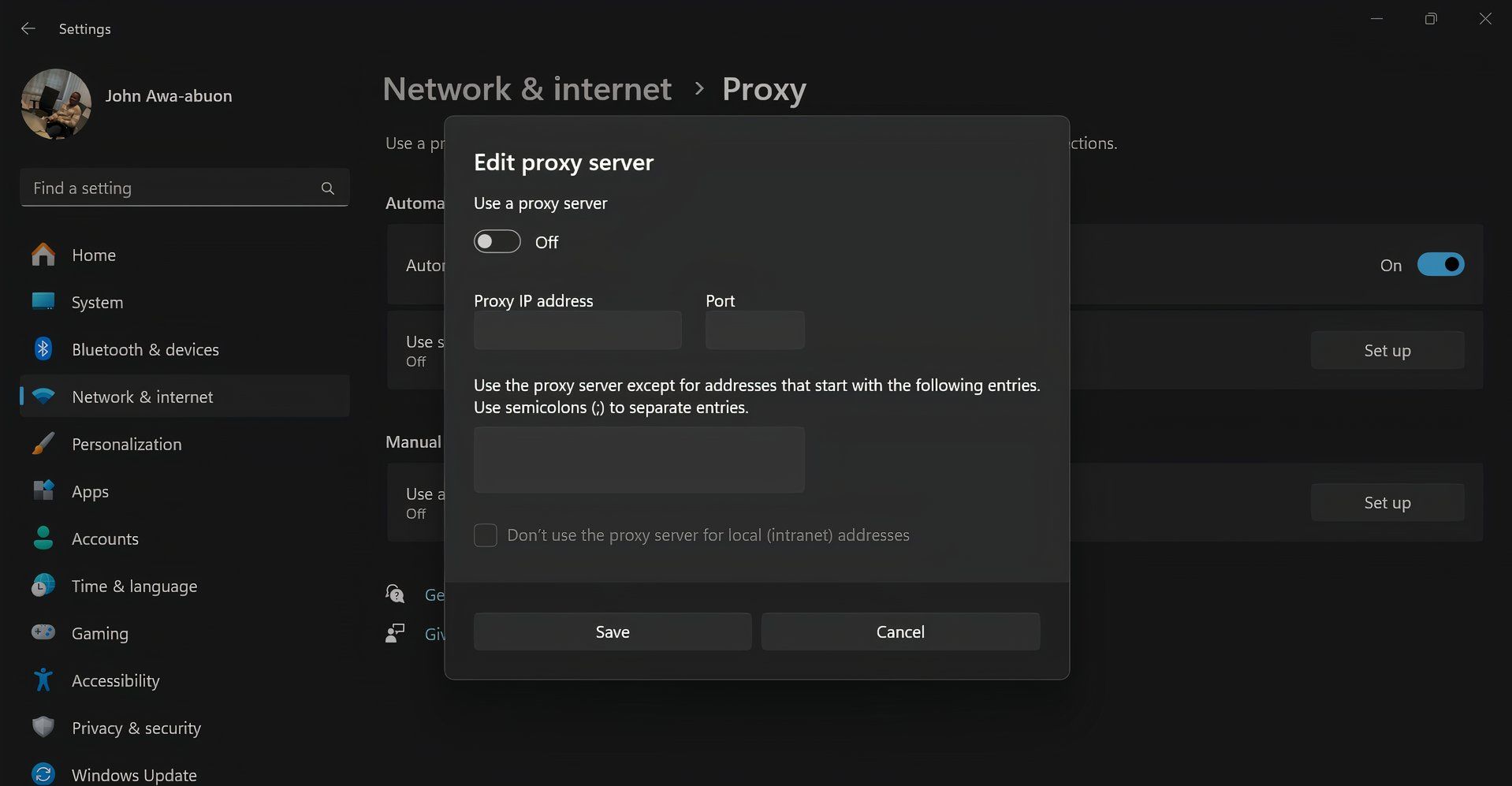
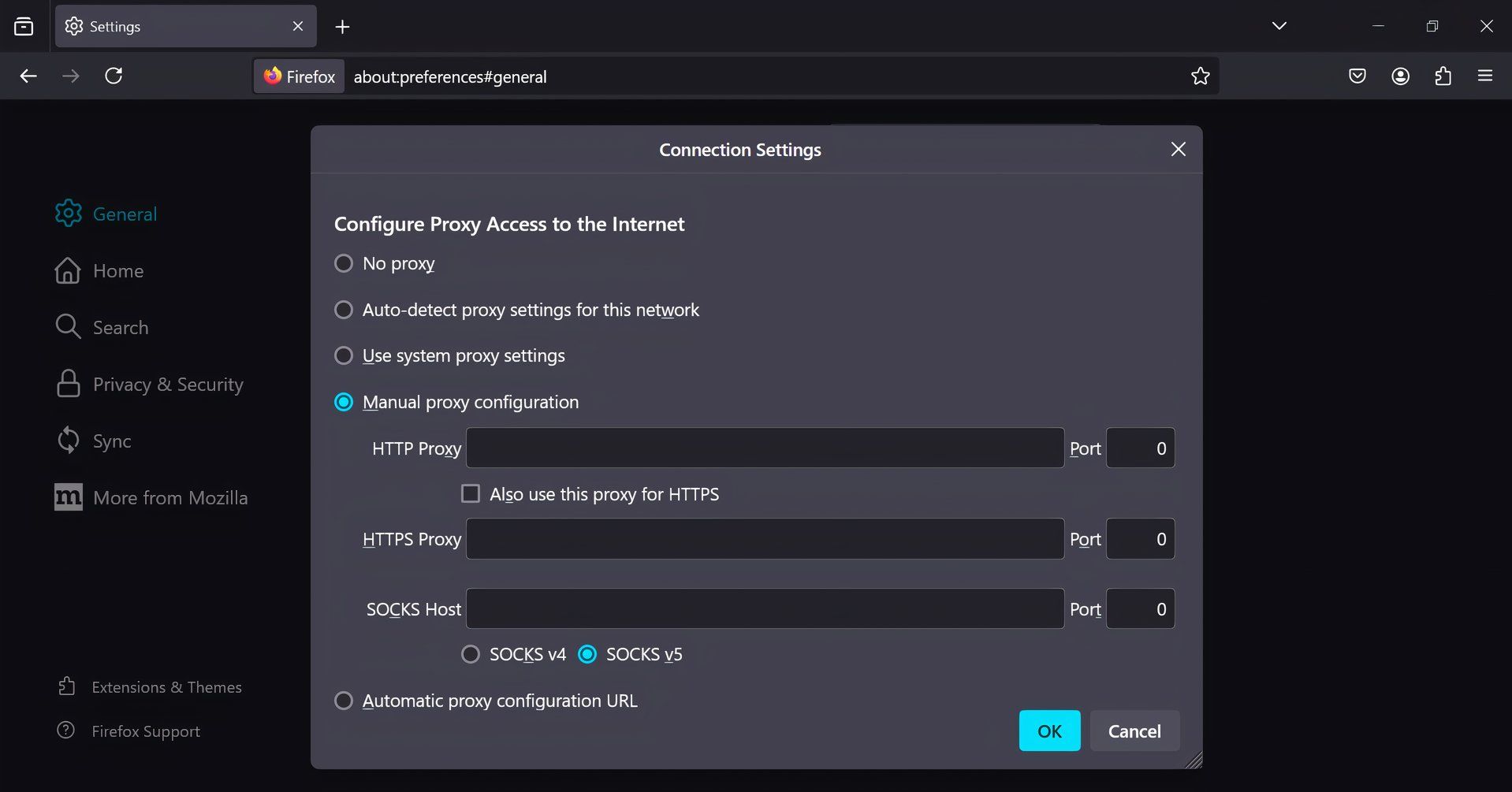
You can set up a proxy server either at the application level—by adjusting individual browser or app settings—or at the system level, where your entire device’s traffic is routed through the proxy. You can do this by configuring your computer’s proxy settings in your operating system, such as through Windows or macOS network settings. Browser extensions are also available for easier access.
Be cautious when selecting a proxy. Public proxies can be prone to slowdowns and expose you to security risks. For better privacy and performance, consider investing in a private proxy service.
3 Browsing With Tor
Tor, short for The Onion Router, is another option for staying anonymous online. It routes your internet connection through a network of volunteer-operated servers, masking your IP address and encrypting your traffic in multiple layers—much like peeling an onion.
The primary benefit of using Tor is its focus on privacy. It makes it extremely difficult for anyone to trace your online activities back to you. This is especially useful for individuals concerned about surveillance or censorship.
That said, Tor comes with some trade-offs. Due to the multiple layers of encryption and routing, your connection speed may be significantly slower than other methods. This makes it less ideal for activities like streaming or gaming. Additionally, Tor provides strong anonymity, but it’s not foolproof—vulnerabilities in your setup or behavior can still expose your identity.
To access the Tor network, simply download the Tor Browser, specifically designed to route your traffic through the Tor network. Install it, and you can start browsing anonymously without additional setup. In that, you’re actually advised to leave the Tor Browser configuration well alone unless you know what you’re doing. Tweaking settings could render its privacy settings useless.
4 Use Remote Desktop
Remote desktop solutions let you control a computer in your desired location through cloud computing. Providers like Amazon Web Services (AWS), Google Cloud, or Microsoft Azure make it simple to rent virtual machines (VMs) in almost any region worldwide.
Setting up a remote desktop requires launching a virtual machine in your desired location through your chosen cloud provider. You can then connect to that VM using remote desktop software like Microsoft Remote Desktop, TeamViewer, or Chrome Remote Desktop.
This approach can be more effective than VPNs for accessing region-restricted servicessince you’re using a real computer in the target location. However, it does require some technical setup and maintaining the security of the remote desktop connection. Ensure you use strong passwords and multi-factor authentication, and keep your VM updated to avoid security vulnerabilities.
5 Use SSH Tunneling
SSH Tunneling, or Secure Shell tunneling, is a method for creating a secure connection between your device and a remote server. Tunneling your internet traffic through an SSH connection encrypts your data and hides your IP address, providing a layer of security similar to a VPN.
This method is popular among tech-savvy users and system administrators. It’s an effective way to securely access remote services, transfer files, and browse the web. Since SSH is widely supported on various operating systems, it can be a versatile tool for secure communications.
While SSH tunneling offers robust security, it does come with some challenges. Setting up an SSH tunnel can be complex for those unfamiliar with the technology. Additionally, it typically requires access to a remote server, which might not be feasible for everyone.